Prior to the pandemic, most businesses were operating in traditional work environments. This meant:
![]() Everyone in the office
Everyone in the office
![]()
All corporate data inside the perimeter (of your office walls) and on corporate devices
![]() Everything behind a firewall
Everything behind a firewall
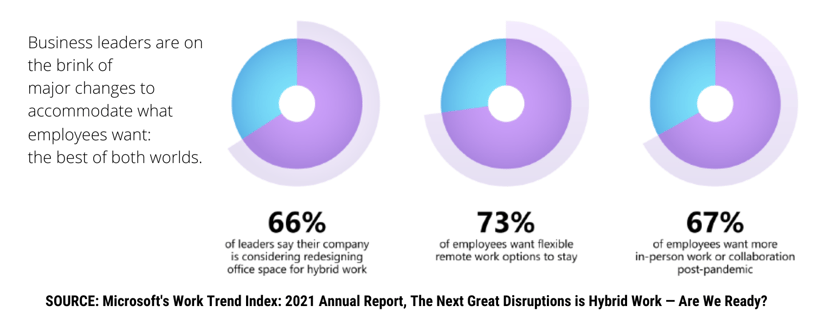
As the dust settles after the largest public health crisis of our life, many businesses are realizing they are never going back to “normal.” Instead, most organizations have concluded that instead of a full-time return to the office, a hybrid workplace is the best way forward. They're also learning that this new hybrid working model has its own challenges — particularly when it comes to IT security.
Article Sections
Your IT Team's Jobs Got Harder
A lot of mid-size businesses that had 3-5 IT team members pre-pandemic are finding that, in this new environment, they can no longer operate at their previous level. And that’s no surprise: the FBI recently reported that cyberattacks have increased by 400% compared to pre-pandemic times.
Many mid-size businesses used to be able to manage IT in-house when their whole staff was in-house, but as the complexity and sophistication of cyberattacks increase, that’s quickly becoming a thing of the past. Organizations having to quickly adjust to support a work-from-home environment created a feeding frenzy for bad actors.
The most significant change organizations have experienced since pre-pandemic is their data is now predominantly in the cloud, rather than all being inside a firewall-protected data center. While IT teams frantically worked to accommodate the new work-from-home set-up, they quickly found out that their traditional security products gave them zero visibility into suspicious activity in the cloud.
Cybercriminals have upped their game, and this means your IT team needs to up its game, too. Your old level of IT resourcing is no longer enough, and it’s more difficult than ever to maintain the required level of expertise because of how threats evolve and change month to month.
Personal Devices Cause Problems
As more data moves to the cloud and the boundaries between work and home continue to blur, mid-size businesses now have more employees working from more locations and using more personal mobile devices.
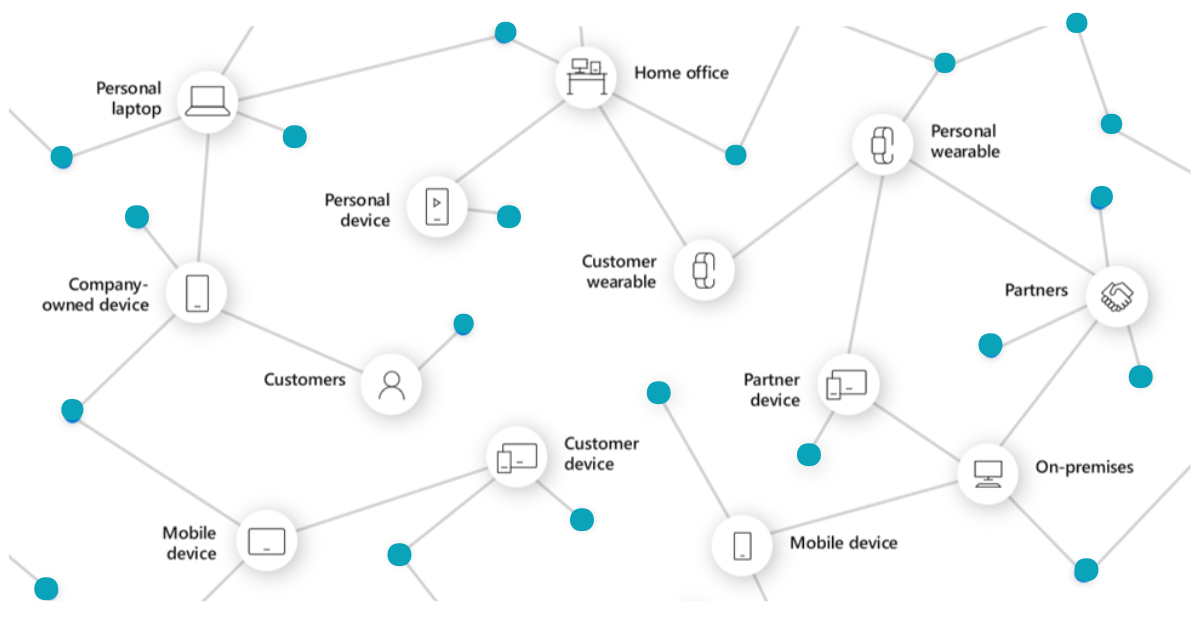
While this shift is convenient for employees who prefer to work away from the office and access this data wherever they go, it also means you have more points of risk to think about. Mobile devices can be lost, and personal devices that may have minimal security installed — or worse, none at all.
You and your employees may think nothing of pulling out your phone or personal laptop to address work issues on the go but doing so effectively doubles the number of endpoints that attackers can target.

Employees who are off the clock still pose risk to your business data if they fall prey to a personal phishing scheme. If they’re also using personal devices for work, they may not think twice about opening a potentially fraudulent personal email while logged into work accounts.
Which brings us to…
Your Employees Haven't Been Trained
Many organizations believe that investing in cybersecurity tools and technologies will guarantee protection for their business. However, the tools you use will only work as well as your team has been trained to use them.
90% of corporate data breaches are a result of employee error, and more than a third of remote workers admit they feel overwhelmed by all the account credentials they need to keep track of. These compelling stats make the case for investing resources in strengthening the weakest link in your cybersecurity chain — your people.
For remote and hybrid workers, security and productivity must go hand-in-hand. If remote security policies cause frustration and wasted time for employees, they will simply work around them. Without employee education and participation, even the most robust security methods aren’t useful or effective.
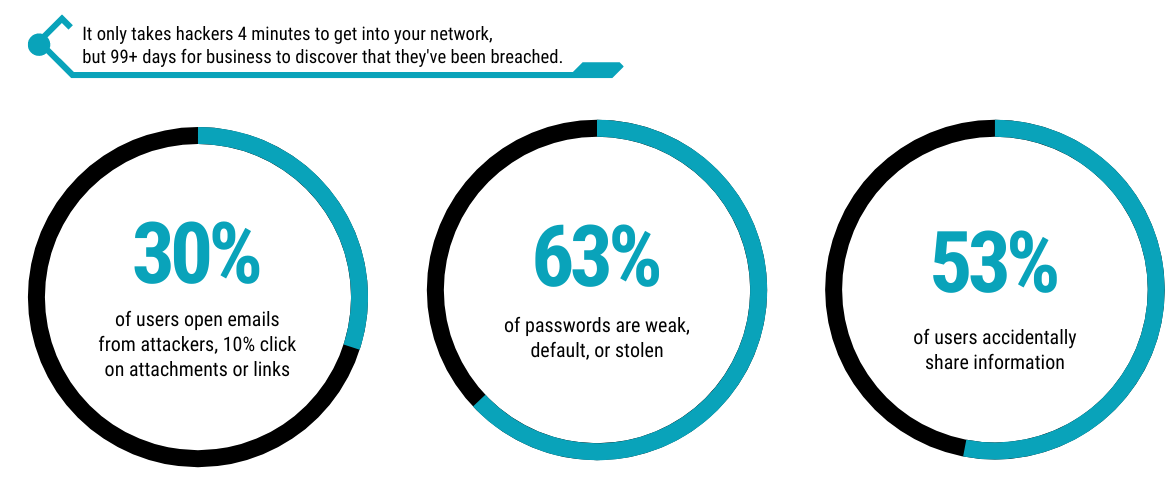
The latest cyberattacks happen fast and are hard to stop. It only takes hackers four minutes to get into your network, but 99 days or more for businesses to discover they’ve been breached. This window of opportunity for attackers could become even wider in a remote or hybrid work environment.

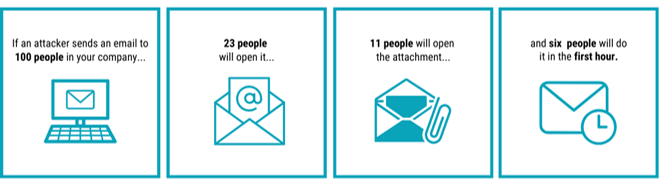
Why Are Attacks So Successful?
IT and Security Team Members are Harder to Recruit and Retain Than Ever Before
As a results of the Great Resignation, recruiting and retaining IT talent just got significantly harder.
In an already competitive space this is no small challenge. If you want to learn more about this topic, we wrote an entire blog post on this subject: CLICK HERE.

How exactly do you weather a perfect cybercrime storm?
As the way we work has evolved, cybercrime tactics have evolved as well. How can you protect your business in an increasingly volatile cybercrime landscape? Take action with this eBook designed to help CEOs, executives, and decision-makers understand today’s cyberthreat and what they can do to tackle today’s challenges and strengthen their security posture.
If you were hit by a ransomware attack, would you know what to do?
On Friday the 13th, in the middle of a pandemic, a cyberattack threatened to bring a city’s entire network—and crucial services—to a halt. Meet the city that refused to pay hackers and learn how quick action, teamwork, and the comprehensive visibility and security of our B365E solution saved the day.
Get Bulletproof Expertise
We're here to help solve your complex IT and security problems.
Get in touch by completing this form and we'll connect you with a Bulletproof expert.


-1.png?width=1000&height=350&name=Impact%20Award%20+%20Global%20Award%20Duo%20Logos%20(5)-1.png)
.png?width=721&name=HubSpot%20Graphic_600X150px%20(2).png)

