Article Sections
How Has The Great Resignation Impacted Technical Jobs?
The average cost of an IT resource is skyrocketing, and the turnover rate is at an all-time high.
Microsoft wrote an excellent article on The Cybersecurity Skills Gap which shares that for every 2 cybersecurity jobs that are filled, 1 sits empty.
As a results of the Great Resignation, recruiting and retaining IT talent just got significantly harder. In an already competitive space this is no small challenge.
Even if you can recruit IT talent, we’re approaching an inflection point where the cost of IT resources is so expensive that insourcing is beginning to make less and less sense. In 2021, salaries have risen in the Information and Communication Technology job sector; with cybersecurity roles leading the pack.

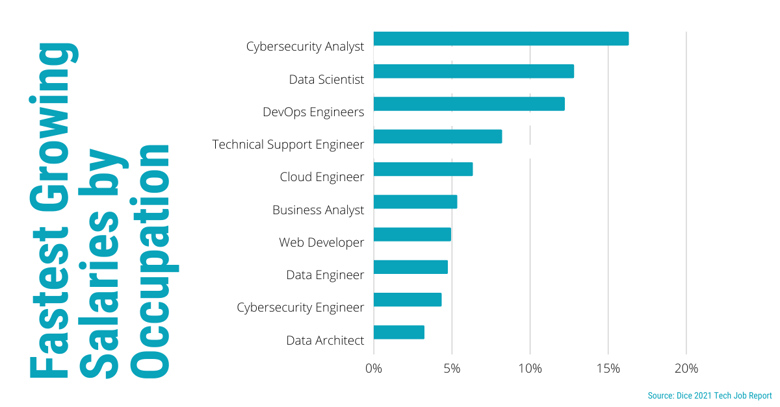
“Additionally, no longer limited to major tech hubs, top-paying companies in the U.S. such as Twitter, VMWare and Google are helping drive up salaries by dipping into the Canadian talent pool.”
– Tech Salary Guide 2022
And now, we’ve reached a tipping point. The cost and difficulty of recruiting IT resources, combined with the inevitable gaps in security posture created by a forced adjustment to hybrid work, leaves organizations vulnerable (not to mention, cyber attacks are at an all-time high).
At organizations with a sufficiently staffed security team, the average cost of a data breach was lower than average by 12.8% but only 38% of organizations surveyed for the 2022 IBM Cost of a Data Breach Report felt their security team was sufficiently staffed.
![]()
How is the Great Resignation Affecting Cybersecurity?
To answer that, we first need to look at how the cybersecurity landscape has evolved and where we are today.
We are currently amid a massive cybersecurity rethink. For the last 30-40 years the best way for organizations to protect themselves was to purchase the “best” of each security point product. However, over time this has led to disconnected security stacks with coverage gaps, unnecessary overlap, and overloading already busy IT departments. This is what we call a “Best-of-Breed” security approach and it also requires customized IT skillsets to maintain.
Here's why the Best-of-Breed is no longer the best approach
- Having multiple security solutions creates complexity which leads to confusion and inconsistency in applying policies and responding to threats. This is a massive risk as the greatest financial impact to an organization happens in the period of time between incident detection and containment. The larger this window is, the more detrimental and costly the attack on your business.
- The Best-of-Breed approach leads to blind spots. Blind spots lead to an increase in risk; you can’t mitigate the incidents you don’t know about. While the Best-of-Breed approach is the illusion of risk reduction, it does not effectively reduce an organization’s risk.
- Lastly, if your organization’s security posture is custom fit; so are the resources to manage it. Whether you’re a small business or an enterprise, hiring the right team to support your Best-of-Breed approach is challenging long term (we talk more about this below).
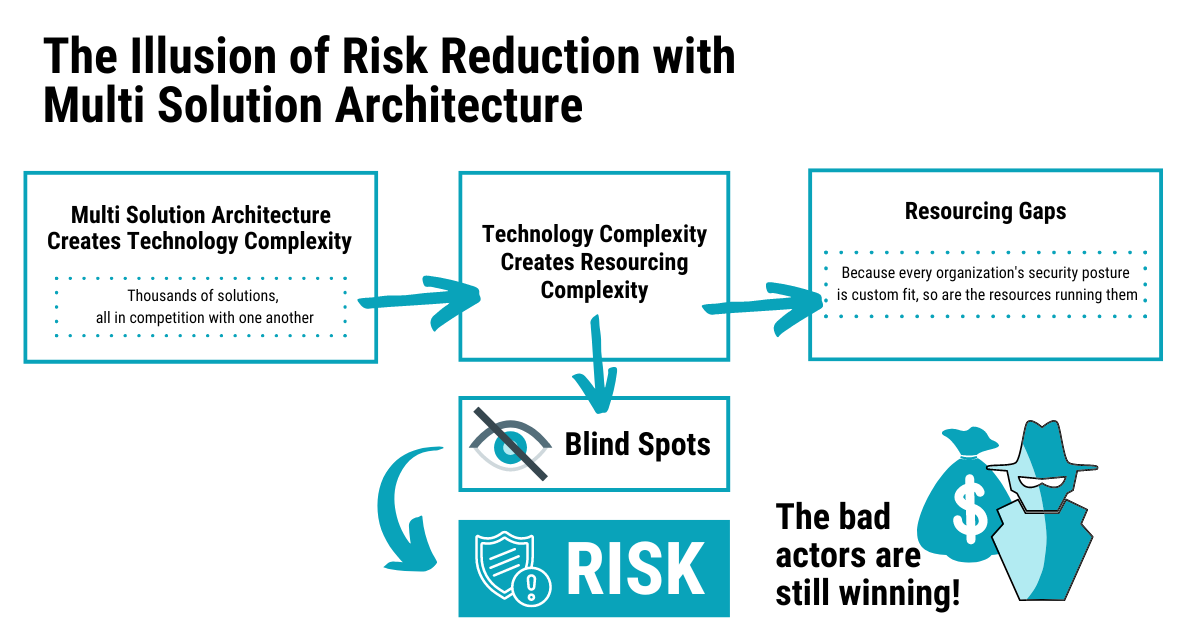
Best-of-Platform is the Future of Cybercrime Protection
While cybercrime has continued to significantly rise year-over-year; the necessary shift to remote or hybrid workplaces over the last two years has accelerated the risk factor amongst all industries.
The brittle and disjointed security systems that were commonplace in many organizations, are an insufficient defense against the volume and complexity of incidents organizations face today.

The fact of the matter is that if you have overlapping security products from multiple vendors, you do have security blind spots, even if you (or your MSSP) are using a SIEM to stitch all those signals together. For more information on the Best-of-Platform approach, check out this blog post. It’s about a 14-minute read, and it contains a ton of useful detail about how the Best-of-Breed approach is leaving businesses vulnerable to costly attacks.
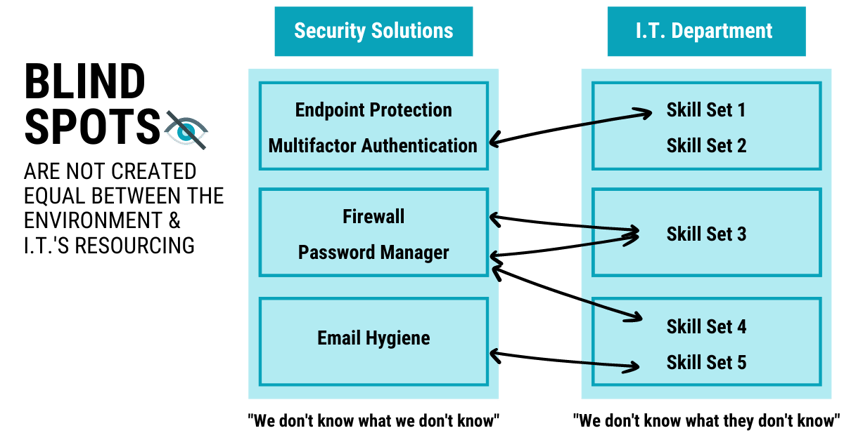
In the image above, the left-hand side shows individual security products while the right-hand side shows the IT skillsets needed to maintain each product(s).
Another way to visualize the diagram is to imagine this being your IT environment, leveraging five different security products and having three different IT resources managing various areas based on their skillset. Setting up a team this way may leave room for gaps where the right resources are not readily available to mitigate blind spots.
What Happens When an IT Person Quits in a Best-of-Breed Security Environment?
The short answer is turnover on your IT team in a Best-of-Breed security environment creates gaps that increase your organization’s risk. As a business leader, you do not want custom, unpredictable resourcing–especially when recruiting IT members is so competitive.
In the recruiting world, Human Resources will often use a term to describe searching for a candidate with a very specific skillset as; “I am looking for a purple haired squirrel.” A security stack IT position that relies on custom resources is, by definition, the perfect purple haired squirrel. And it’s inherently volatile because when there’s turnover on your IT team and only a handful of people can fill those specific roles, your organization is left unprotected.
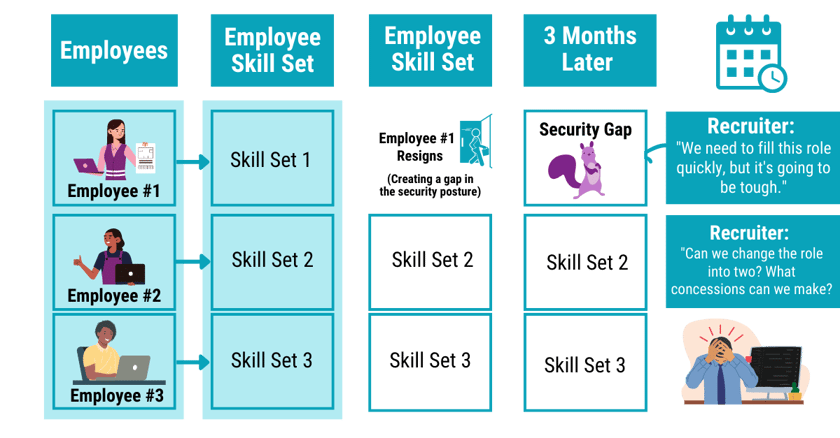
As the diagram above shows, the longer it takes for your organization to fill the open IT position(s); the longer your organization is vulnerable to cyberattacks. Companies can’t continue to patch together security—you’ll never be protected.
What Can Organizations Do to Protect Themselves?
What we have learned–and lived–is that the true “best” security posture is one that tightly integrates to provide a complete, holistic picture of the organization, with no overlap or conflict in the process for investigation of or response to incidents.
Smart organizations are beginning to rethink their security posture. If you aren’t sure where to start, the best next step is to get an assessment to understand where your organization stands today and what security gaps currently exist for your organization.

How exactly do you weather a perfect cybercrime storm?
As the way we work has evolved, cybercrime tactics have evolved as well. How can you protect your business in an increasingly volatile cybercrime landscape? Take action with this eBook designed to help CEOs, executives, and decision-makers understand today’s cyberthreat and what they can do to tackle today’s challenges and strengthen their security posture.

Microsoft Defend Against Threats with SIEM + XDR Workshop
Gain visibility into immediate threats across email, identity, and data and demonstrate how Microsoft Sentinel and Microsoft 365 Defender help organizations use intelligent security analytics and threat intelligence to detect and quickly stop active threats.
Cyberattacks have increased by 400% compared to pre-pandemic times. Is Your business prepared?
Cybersecurity is no longer simply an issue for your IT team. It’s time for other members of your organization to start sitting at the cybersecurity decision-making table. This eBook can help you understand modern cyberthreats and their potential impact on your business.
Get Bulletproof Expertise
We're here to help solve your complex IT and security problems.
Get in touch by completing this form and we'll connect you with a Bulletproof expert.


-1.png?width=1000&height=350&name=Impact%20Award%20+%20Global%20Award%20Duo%20Logos%20(5)-1.png)