
You can buy just about anything “as a service” now. The best and most widely understood example is software-as-a-service (SaaS); we used to pay a large perpetual licensing fee for a suite of software, but now it’s sold on a subscription basis with completely cloud-based delivery. This same “as-a-service” delivery model is putting the tools to commit cybercrime in the hands of just about anybody who wants them, and mid-size businesses are their #1 target.
![]()
![]()
Article Sections
After reading Microsoft’s latest reports, here are the key takeaways every business leader should know:
The Cybercrime Economy is Growing
Cybercriminals are highly motivated because they know there is a lot of money to be made at your expense. It used to be that only attackers with advanced hacking skills could pose a threat to your business. These days, all the building blocks of a successful attack can be purchased online just about as easily as you can order dinner.
Amateur threat actors can turn to a growing cybercrime supply chain to obtain attack kits, phishing-as-a-service, stolen credentials, customized “lead generation” lists of potential victims, and more. Cybercriminals have even created their own affiliate programs, providing all the elements of a successful attack in exchange for a percentage of stolen money.
All of this means that it no longer takes much skill to successfully pull off a cyberattack. Taking cues from the gig economy, the most skilled threat actors simply provide an attack-in-a-box and then watch profits pour in while aspiring cybercriminals assume the majority of the risk.
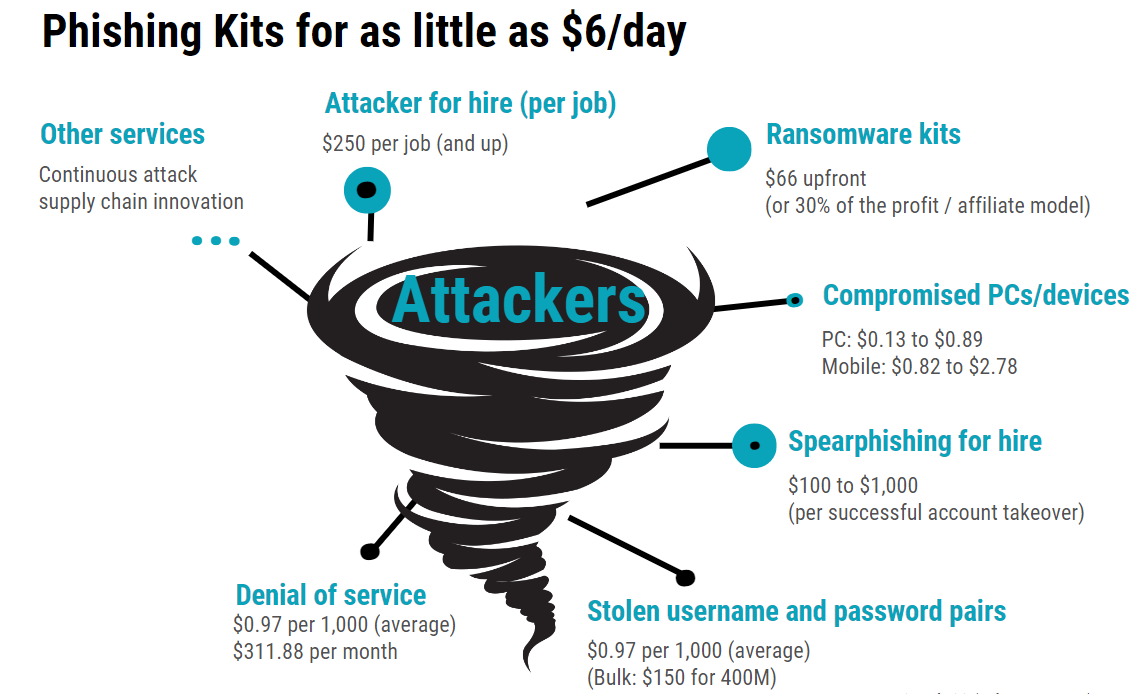
Ransomware is a Booming Business
The cybercrime “gig economy” has experienced its largest growth in the area of ransomware attacks. Ransomware-as-a-service (RaaS) is likely the most pressing threat to business leaders today. Thousands of companies have fallen prey to this kind of attack, and they’re not alone. In May 2022, Costa Rica declared a national emergency after its government organizations were hit with a widespread ransomware campaign.
A ransomware attack involves an attacker deploying malware that encrypts and steals your corporate data, holding it ransom for whatever sum of money the attacker demands. The average ransom demand doubled in the past year*, which is saying something considering the 2021 average was over $200,000. Not a bad return on investment for ransomware kits that can be purchased for less than $100.
Most business leaders have a talent for being able to identify threats to their businesses long before the danger is imminent. Unfortunately, this just isn’t the case for ransomware attacks. According to data collected by Microsoft, nearly 97% of all successful ransomware attackers can infiltrate their target in under four hours. And, of course, cyberattackers aren’t constrained to traditional business hours.
Ransomware is when a hacker takes control of your data and prevents you from accessing it.
Access to your own files is only returned when you pay the ransom they demand.
![]()
Your Identity is For Sale
Phishing is still a huge threat to mid-size businesses without the proper security protocols — including ongoing employee training — in place. Phishing attacks are also becoming more sophisticated, more automated, and easier for amateur cybercriminals to deploy.
There are entire online organized crime networks dedicated to Business Email Compromise (BEC). Unsuspecting employees can be led to convincing-looking login pages that record their credentials to be used in an attack or sold online. And just like your sales team might enrich lead lists with additional data, services that pad out a victim’s stolen identity credentials will add information like company name, seniority level, and industry association.
Stolen credentials are a goldmine for threat actors. Why would a hacker try to break into your network when they can simply log in? Even one compromised login can lead to all of your organization’s sensitive customer data, financial information, or other confidential information becoming available to an enterprising cybercriminal.
You may not become aware of a stolen digital identity for quite some time. After credentials are stolen, a number of things might happen:
- The attacker may create a backdoor account to provide permanent access into your network, and then “rent out” that access to whoever is willing to pay.
- Lower-value credentials might be listed for bulk sale on the dark web.
- The attacker might “camp out” in your network, sending malicious messages to your trusted contacts and farming more victim leads that they can then turn around and sell, or collecting other types of data to enable a more widespread attack.
Phishing is a social engineering tactic that involves sending fraudulent emails to individual employees.
These emails, which are often very sophisticated and convincing, often ask recipients to log in to a business account on a fake landing page and then steal their credentials.
![]()
![CEOC-Suite eBook 2023 Refresh [Dark & Stormy]](https://content.bulletproofsi.com/hs-fs/hubfs/CEOC-Suite%20eBook%202023%20Refresh%20%5BDark%20%26%20Stormy%5D.png?width=2000&height=1152&name=CEOC-Suite%20eBook%202023%20Refresh%20%5BDark%20%26%20Stormy%5D.png)
Cybercrime is Political (Even if You're Not in Politics)
The past few years have been marked by a quickly changing geopolitical landscape. Conflicts within or between various countries have created new opportunities for nation-state actors — cybercrime organizations that are backed by foreign governments. They’re well-funded and capable of coordinating sophisticated attacks.
An unprecedented number of nation-state threats have been identified since the beginning of the COVID-19 pandemic. Many originate from Russia, North Korea, China, and Iran; and Russia’s invasion of Ukraine in February 2022 ushered in a new era of cyber-warfare, as nation state actors “are using advancements in automation, cloud infrastructure, and remote access technologies to attack a wider set of targets” with increased sophistication.
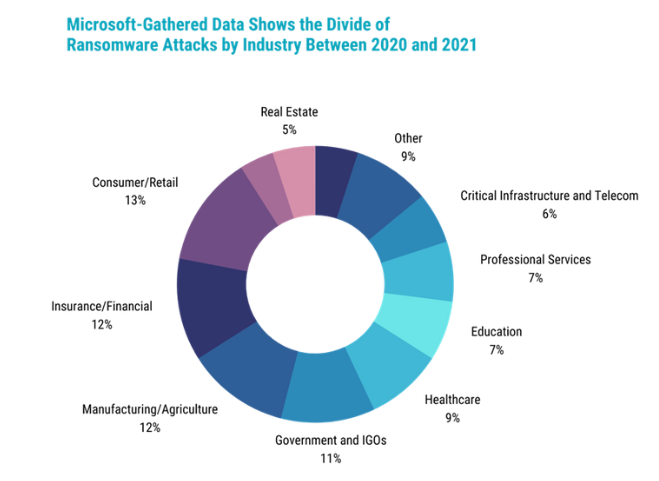
Government organizations like diplomatic and defence entities, of course, are particularly vulnerable to this kind of attack. However, nation-state actors don’t just go after other governments. Microsoft has also seen an increasing number of attacks carried out against energy and utility companies, higher education, economic/financial organizations, law firms, medical research facilities, and healthcare providers. The motivations for attacking these types of businesses range from their proximity to government organizations to their ability to pay up after a ransomware attack, bringing in even more funding for these threat actors to go after critical infrastructure.
Internet of Things is a Major Risk Factor
Attackers can target any internet-connected device, not just your work computer or laptop. In some workplaces, this might be something like a connected TV or a smart security system. In others, Internet of Things (IoT) devices could include critical pieces of equipment, with disastrous consequences if they are compromised.
High-profile examples include the Oldsmar water hack, where cybercriminals attempted to poison the water supply in a Florida town of 15,000 by upping levels of sodium hydroxide to life-threatening levels. The attackers were able to increase levels of sodium hydroxide, also known as lye, from 100 to 11,100 parts per million. They did this by exploiting a vulnerability in the water plant’s SCADA system — a control system architecture used to manage industrial equipment. Fortunately, an operator noticed the intrusion and was able to manually intervene before anyone got hurt.
Cybercriminals can gain unauthorized access to any connected system, including security cameras, medical equipment, and industrial control systems. As businesses become more connected, they also become more vulnerable to devastating attacks.
![]()
Cybercrime is Big Business
These reports compiled by Microsoft — based on the real data their security teams analyze every day — illustrate just how structured and coordinated today’s cybercriminals really are. Like you, they run a business. Unlike you, they don’t play by the rules.
Are you an easy mark for a well-organized cybercrime network? Will they see you as low-hanging fruit? A huge percentage of organizations just don’t have the security protocols in place to stop them, or the in-house expertise to know where to start. You’ve got to hand it to modern-day attackers: they certainly know their target market.
There is one more significant takeaway from the latest Microsoft reports, and it’s extremely relevant to business owners in a post-pandemic world. Unless your business absolutely requires employees to be physically present, it’s likely that you shifted to remote work at least temporarily. Many businesses still haven’t fully returned to in-person work, and many don’t plan to.
Remote or hybrid work environments are a huge risk factor for falling victim to a cyberattack. If your organization rushed to implement remote work policies in early 2020, you may have created security gaps that still linger, waiting to be discovered by an attacker. In this blog post, How Forced Hybrid Work Created Vulnerable Businesses, we dive deep into how remote and hybrid work environments create cybersecurity risk (and what you can do about it).

Microsoft Defend Against Threats with SIEM + XDR Workshop
Gain visibility into immediate threats across email, identity, and data and demonstrate how Microsoft Sentinel and Microsoft 365 Defender help organizations use intelligent security analytics and threat intelligence to detect and quickly stop active threats.

How exactly do you weather a perfect cybercrime storm?
As the way we work has evolved, cybercrime tactics have evolved as well. How can you protect your business in an increasingly volatile cybercrime landscape? Take action with this eBook designed to help CEOs, executives, and decision-makers understand today’s cyberthreat and what they can do to tackle today’s challenges and strengthen their security posture.
Get Bulletproof Expertise
We're here to help solve your complex IT and security problems.
Get in touch by completing this form and we'll connect you with a Bulletproof expert.


-1.png?width=800&height=280&name=Impact%20Award%20+%20Global%20Award%20Duo%20Logos%20(5)-1.png)

