Introduction
Cybercrime On The Rise
Experts predict that by 2021, cybercrime will cost the world $6 trillion annually and businesses will fall victim to a ransomware attack every 14 seconds.* Add to that the World Economic Forum’s Global Risks Report 2019 lists data fraud or theft and cyber-attacks as a top-five risk to society alongside natural disasters and extreme weather.
With the ever-increasing frequency and complexity of cyber-attacks, it's no longer a question of if your Tribe will be targeted, it's a matter of when. With complex business practices, Tribes need to strengthen their security more than ever. That's why Bulletproof is here to help you develop a security platform that will protect your Tribal data and digital assets from cyberattacks!
*Cybersecurity Ventures Report
![]()
The average data breach goes undetected for around 200 days.
On top of that, the FBI seen a 400% increase in cyberattacks post-COVID-19 targeting all enterprises, even Tribes.
Table of Contents
Tribal Enterprises and Cyber Criminals

Securing Your Tribal Enterprise For A Better Tomorrow
Committed to keeping your Tribal data and digital assets secured
Our knowledge of Tribal gaming and understanding of casino systems provides tremendous value to Tribal enterprises. Our comprehensive portfolio of best-in-class solutions includes significant expertise in cybersecurity, enabling us to bolster our existing security services for the Tribal enterprises. When you compliment your existing resources with our deep technical proficiency and the expertise of our industry-certified IT professionals, the result is tailored solutions that meet your specific business needs at a fraction of traditional in-house setup costs. Companies rely on us for accurate and up-to-date professional risk assessment, audit, testing, and advisory services. Our Bulletproof team is here to support you every step of the way.

Managed Security Solution To Solve Your Tribal Enterprise Challenges
Security can no longer be viewed as an extra layer of a business protocol. CIOs are worried about breaches, their organization’s reputational risk and protecting their client data. These risks are becoming more and more financially and operationally impacting as well. Security must become embedded in organizations’ core business framework. With the growing cybercrime landscape, threats to private or intellectual property, and the ever-increasing fallout associated with security incidents, failing to implement the appropriate countermeasures can be hazardous.
Our managed security services were specifically designed to support the Tribal enterprises in its fight against cyber attacks and cyber crime. The word “managed” simply means that we look after this service or function for you. As a trusted partner, we take the load off your team’s shoulders, providing active monitoring around the clock with our 24/7 services. The services are flexible and customizable to meet your needs and budget, whether you are just getting started with IT security to comply with audit requirements or you are looking for advanced services to monitor every aspect of your network and customer data.
We have completed hundreds of projects for a wide cross section of public sector and commercial clients. Even more relevant is our understanding of Tribal enterprises. When it comes to security experience, our resources are second to none, and we hold the highest levels of industry certification.

To help tribal enterprises protect their data, we offer a suite of comprehensive managed security services including:
| Real-Time 24/7 Monitoring and Incident Management |
| Security as a service |
| Firewall Monitoring and Management |
| Digital Forensics Investigation and Cyber Incident Response |
| Security Management System |
| Bulletproof 365 - Productivity & Security for SMBs |
| Bulletproof 365 Enterprise - Advanced Security Protection for Midmarket/Enterprise Organizations |
| Security Aware - Employee Cyber Risk Awareness Service |
OUR STATE-OF-THE-ART SOC FACILITY IS DEDICATED TO STRENGTHEN YOUR IT SECURITY
Our SOC is a state-of-the-art facility custom built to provide our managed security services. Our managed security team protects clients on 6 continents. Businesses of all sizes, including Tribal enterprises choose managed security service for a variety of mission-critical reasons.
With the increasingly dangerous threats facing the Tribal enterprises (more powerful hackers and more sophisticated attacks), coupled with a dramatic shortage of qualified cybersecurity professionals, organizations need a reliable partner to help. By providing these security services in a “managed” offering, customers of all sizes can gain access at a fraction of the cost they would incur by building their own infrastructure and team.
We take the load off your people and resources, giving you 24/7 dedicated cyber security vigilance with our Managed Security Service. We know how vulnerable the industry is. Over the years, when testing for security, our people penetrated more than 220 casinos and lotteries with a 90% plus success rate.
We use our industry know-how to actively develop threat detection rules specifically around Tribal enterprise systems. And with experts like our PEN testers, who continually test vulnerabilities every day, we do more than secure our clients, we make their security better, stronger, and more secure than ever.
![]()
Bulletproof’s cybersecurity experts can monitor your systems more efficiently, analyze volumes of data more effectively and respond more rapidly, helping ensure any potential cyberthreats don’t get past our defenses.

Cybersecurity Solutions To Minimize Tribal Enterprises Risk & Maximize Confidence
Cyber threats can come from external and internal sources. Either way, the fallout from a security breach can be catastrophic. And if you operate in a sensitive or complex industry, your risks are amplified. We offer a wide range of cybersecurity solutions to help Tribal enterprises identify risks throughout your business operations. Not only will we help identify the risks and threats, but we will provide the right solutions to help you correct the risks for a better tomorrow.
Whether you've been the victim of a breach, worry that your last security audit was lacking or you require a risk assessment as part of financial or operational audit requirements, Our vulnerability and penetration assessments are a powerful tool to help you proactively manage those risks.

| Protect your Tribal enterprises' reputation against lost shareholder, customer, and public confidence |
| Protect intellectual property (IP) from external and internal threats |
| Detect breaches and risks quicker and know if threats are real or "false positives" |
| Safeguard against insider theft, fraud or malicious activity |
| Validate network security and the safety of customer |
| Comply with vulnerability & penetration testing requirement as part of your financial audit |
| Gap Assessment helps you prepare for a PCI audit |
CYBERSECURITY SOLUTIONS:
Internal & external network vulnerability assessments and penetration testing
Bulletproof will gather all possible known vulnerabilities against a published vulnerabilities database and scan all ports for possible areas that will help a hacker gain access to the property network.
Wireless network vulnerability assessments
Bulletproof will completely map all wireless access points that are on the property at the time of the assessment. Through this assessment we will be able to identify access points that might be on the network that are not authorized to be there.
Social engineering
Social engineering can be broken into two types: human-based and technology-based. Human-based refers to a person-to-person interaction to obtain the desired action. Technology-based refers to having an electronic interface that attempts to retrieve the desired outcome. Within in these two types of attacks there are numerous attack techniques that can be used.
Web application security assessments
Bulletproof will validate the security of the submitted application. This will enable Bulletproof to identify possible vulnerabilities or holes in the application that a potential hacker might use to circumvent the intended operation of the application. Our Web application testing methods are used in conjunction with the OWASP methodology.
IT security policy and procedure reviews
Bulletproof applies a holistic approach to assessing your organization's information security policies and procedures. Bulletproof integrates our understanding of your security goals with our experience in achieving best practices compliance. Bulletproof verifies that your policies conform to the controls established in the ISO 27001 Industry Leading IT Security Standard. The goal of every information security program is to maintain the confidentiality, integrity, and availability of data.
PCI Health Check
Bulletproof will review as a combination of documentation/evidence review and onsite discussions. We will identify documentation that we require for review prior to the planning meeting and during the scope validation exercise.
Virtual Chief Information Security Officer
Through our vCISO service, you can leverage a block time retainer with a CISO to advise on governance and policy, security architecture, incident response and remediation, or vendor selection of IT Security products. A vCISO provides all the benefits of a CISO without the associated overhead costs. Our vCISO service gives you direct access to top tier security experts, who will manage you through your cybersecurity program, working for your organization and ensuring your information stays secures, reducing the risk – and exposure – of a cyber-attack.

Quality Assurance & Testing To Reduce Your Time-to-Market, Lower Costs, and Mitigate Risk
Quality is never a coincidence. Producing top-tier products takes time, calculated effort, and expertise that’s derived only from years of experience. Furthermore, when you’re dealing with software in an increasingly complex digital landscape, security needs to be a top priority to mitigate risk. For large or complex projects, you need a team of professionals who can bring strategic thinking, objectivity, and a strong regard for security to the table.
Bulletproof’s QA & testing team brings an unbiased perspective to your QA practices. We assess your processes, identifying gaps and opportunities for optimization. Then, we deliver a formal report which outlines our findings and strategic recommendations, including an improvement roadmap that will help you take the right next steps.
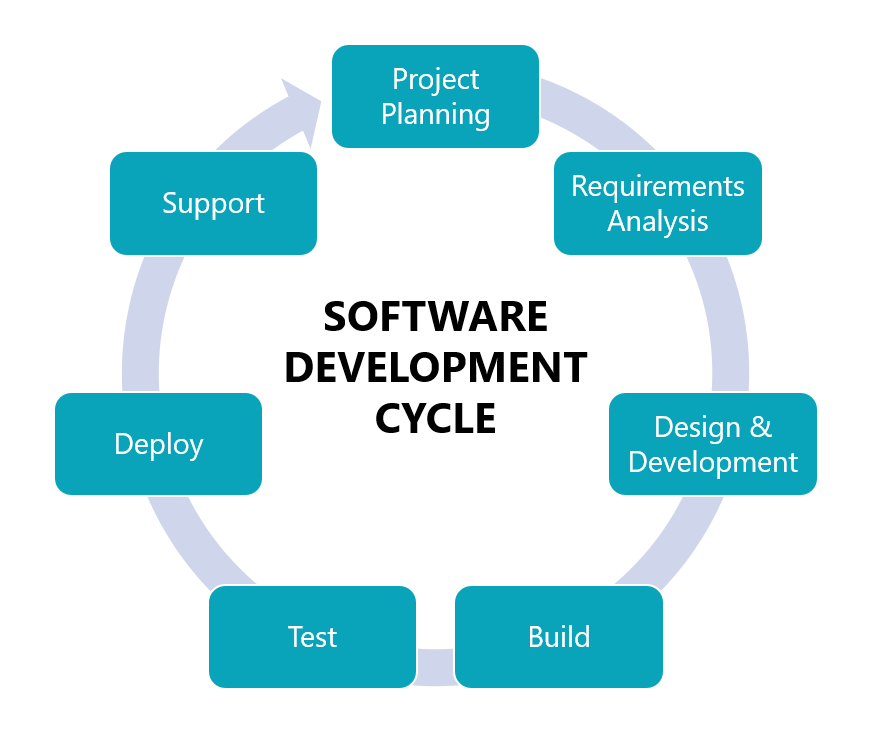
Bulletproof offers the following solutions to meet your Tribal enterprise needs:
| Functional Testing | This type of testing is the process of applying industry best-practice testing methodologies to support today’s development processes. Some test methodologies employed include: system integration, user acceptance, mobile, compatibility and interoperability, usability, localization, and data warehousing BI testing. This testing is performed against the business and system requirements of the application and involves the complete integration of the end-to-end system. |
| Performance Testing | Our performance testing is the process of evaluating an application or system against performance requirements through analysis, tuning, optimization or refactoring. This testing includes validating response times, throughput and finding breaking points using load, stress, endurance, volume and scalability testing techniques. |
| Test Automation | Process of automating repetitive but necessary tests in a formalized testing process such as regression tests but does not replace manual testing. The automation tests augment the testing suite to improve test coverage, efficiency and speed to market. |
| QA Assessment | Process of providing an independent review of the Quality Assurance and Quality Control processes employed in the SDLC to determine the methodologies, processes, policies and procedures that may or may not be in place. At the conclusion of a QA Assessment, a report of findings including an Improvement Roadmap, will be provided with recommendations for implementation. |

ON-DEMAND WEBINAR: How To Protect Tribal Data & Digital Assets From Modern Cyber Threats
How Confident Are You That Your Data & Digital Assets Are Secure?
The FBI has seen a 400% increase in cyberattacks post-COVID19 targeting all enterprises, even Tribes! With the ever-increasing frequency and complexity of cyberattacks, it's no longer a question of if your Tribe will be targeted, it's a matter of when.
-1.png?width=350&height=250&name=HS%20CTA%20Graphics%20(1)-1.png)
Make the Most of Your Microsoft Investment with Support from a Microsoft Solutions Partner
Get in Touch with Bulletproof Today
Bulletproof is headquartered in Canada with offices across the United States and around the world. Technology is inextricable to the way lottery, gaming organizations, & Tribal enterprise and gaming operate–which poses both opportunities and challenges, especially in highly-regulated industries. Bulletproof works with lotteries, top gaming operators, suppliers, and regulators, and Tribal enterprise & gaming across United States, Canada, and EMEA to leverage their extensive industry experience and IT know-how to reduce risk and improve client processes, systems, education, and business infrastructure.
Named Security Microsoft Partner of the Year globally in 2021 and three-peat Microsoft Canada IMPACT Award Winner [2021-2019], Bulletproof is proud to be a long-standing Microsoft Gold Partner with twelve gold competencies, a member of the Microsoft Intelligent Security Association (MISA), and holder of the Microsoft Threat Protection Advanced Specialization.
For more information on Bulletproof join us on Facebook, Twitter, and LinkedIn.

![Microsoft Partner of the Year [POTY] Logo_White Transparent Microsoft Partner of the Year [POTY] Logo_White Transparent](https://content.bulletproofsi.com/hs-fs/hubfs/Microsoft%20Partner%20of%20the%20Year%20%5BPOTY%5D%20Logo_White%20Transparent.png?width=500&height=183&name=Microsoft%20Partner%20of%20the%20Year%20%5BPOTY%5D%20Logo_White%20Transparent.png)


