Prior to the pandemic, most small businesses were operating in traditional work environments which meant:
![]() Everyone in the office
Everyone in the office
![]()
All corporate data inside the perimeter (of your office walls) and on a corporate device
![]() Everything behind a firewall
Everything behind a firewall
The pandemic forced businesses to scramble to manage a sudden shift to remote work. Plans — and mistakes — were hastily made. Ad-hoc solutions were implemented, and IT departments, if they existed, were stretched far beyond their limits.
While IT teams frantically worked to accommodate the new work-from-home set-up, they quickly discovered that their traditional security products gave them zero visibility into suspicious activity on their cloud network.
As the dust settles after the largest public health crisis of our lifetime, many small businesses realize they are never returning to “normal.” Instead of a full-time return to the office, many businesses have chosen a hybrid workplace as the best way forward.
Small businesses used to be able to manage IT in-house, but as the complexity and sophistication of cyber threats increase, that’s quickly becoming a solution of the past.
Top 6 Things You Need to Know
#1 Attackers Don't Just Go After Big Businesses with Big Money
In fact, they know that small businesses are much less likely to have sufficient cybersecurity measures in place, making them the path of least resistance and a much easier target.
58% of security breaches happen to small businesses, and many don't have the resources to survive the financial and reputational damage a breach may cause. Hackers continuously monitor the entire market for areas of vulnerabilities and often target smaller companies precisely because they know those businesses have underinvested in cybersecurity.
It’s also worth considering that cybercriminals will bring the same level of sophistication to attacking an SMB company as they do a large Fortune 500 enterprise — and because the first phase of the hacking process is automated, they will come at your company just as hard.
#2 Hybrid Workplace are Here to Stay: How to Keep Your Team Productive and Secure
The most significant change organizations have experienced since pre-pandemic is their data is now predominantly in the cloud, rather than all being inside a firewall-protected data center.
With data moving to the cloud and increased mobile access, small businesses now have more mobile devices and employees are working from more locations. While that’s good news for employees who can access this data wherever they go, it also means you have more points of risk to think about.
Your team is now using more mobile devices that they can lose. They’re also using personal devices that may have minimal security installed or worse, none at all. Plus, phishing, ransomware, and social engineering tactics have become more sophisticated and harder than ever to recognize.
Cybercriminals have upped their game, which means you need to up your game too. Understandably, you don't have time to become a cybersecurity expert, and even if you did, it’s even more difficult to maintain that level of expertise because of how threats evolve and change month to month.
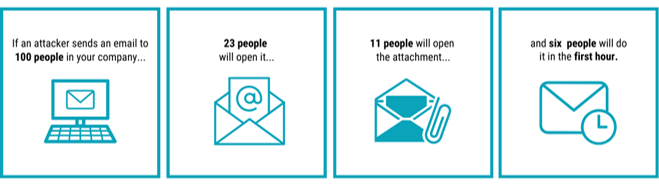
90% of ransomware attacks start with a phishing email. Does your organization have the modern security features required to prevent phishing emails with dangerous links from getting through to your users?
#3 The Cybercrime Economy is Growing
Cybercriminals are highly motivated because they know there is a lot of money to be made at your expense. It used to be that only attackers with advanced cybersecurity skills could pose a threat to your business. These days, all of the building blocks of a successful attack can be purchased online just about as easily as you can order dinner.
Even amateur threat actors can turn to a growing cybercrime supply chain to obtain attack kits, phishing-as-a-service, stolen credentials, customized “lead generation” lists of potential victims, and more. Cybercriminals have even created their own affiliate programs, providing all of the elements of a successful attack in exchange for a percentage of stolen money.
All of this means that it now takes very little skill to pull off a cyberattack successfully. Taking cues from the gig economy, the most skilled threat actors simply provide an attack-in-a-box and then watch profits pour in while aspiring cybercriminals assume most of the risk.

#4 Ransomware is a Booming Business
The cybercrime “gig economy” has experienced its largest growth in the area of ransomware attacks. Ransomware-as-a-service (RaaS) is regarded as one of the most pressing threats to business leaders today. Thousands of companies have fallen prey to this kind of attack. For example, Costa Rica declared a national emergency in May 2022 after its government organizations were hit with a widespread ransomware campaign.
A ransomware attack involves an attacker deploying malware that encrypts and steals your corporate data, holding it ransom for whatever sum of money the attacker demands. The average ransom demand climbed to over $200,000 in 2021 — not a bad return on investment for ransomware kits that can be purchased for less than $100.
Most business leaders have a talent for being able to identify threats to their businesses long before the danger is imminent. Unfortunately, this just isn’t the case for ransomware attacks. According to data collected by Microsoft, nearly 97% of all successful ransomware attacks can infiltrate their target in under four hours. And, of course, cyberattacks aren’t constrained to traditional business hours.
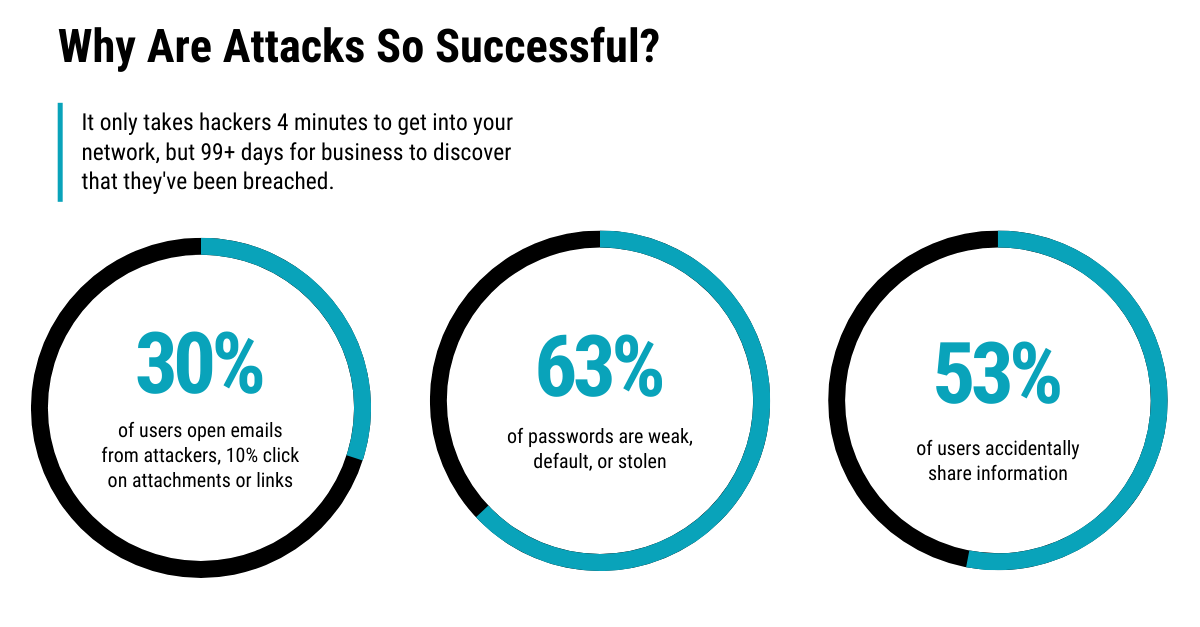
#5 New Cyberattacks Can Wipe Out A SMB In Under 4 Minutes
The latest cyberattacks happen fast and are hard to stop. It only takes hackers 4 minutes to get into your network, but 99+ days for a business to discover they’ve been breached.
#6 IT and Security Team Members Are Harder to Recruit and Retain Than Ever Before
![]() The average cost of an IT resource is skyrocketing, and the turnover rate is at an all-time high.
The average cost of an IT resource is skyrocketing, and the turnover rate is at an all-time high.
Microsoft wrote an excellent article on The Cybersecurity Skills Gap which shares that for every two cybersecurity jobs that are filled, one sits empty.
“... by 2025 there will be almost 3.5 million open cybersecurity jobs globally – a 350% increase over an eight-year period.”
Source: Tech Issues Explained -The Cybersecurity Skills Gap by Microsoft
As a results of the Great Resignation, recruiting and retaining IT talent just got significantly harder. In an already competitive space this is no small challenge.
“With the hiring freezes of 2020, followed by the widespread implementation of technology demanded by digital transformation, this 2021 surge in Canadian tech jobs has led to unparalleled demand and competition for talent both on and off the market.”– Tech Salary Guide 2022
If you’re interested in learning more about this topic, we wrote an entire blog post on this subject: CLICK HERE.
What Can You Do?
Small businesses today face a challenging I.T. environment. A firewall, antivirus software, email filtering, and backup used to be enough to protect a small business. But now that so many more employees work remotely — creating the necessary move to store your sensitive corporate data to the cloud — the threat landscape has drastically changed.
With the reality that cybercrime is hitting every industry and quickly, if you are a small business owner or executive, get a sense of your vulnerabilities with a cybersecurity briefing.
To claim your complimentary 20-minute, one-on-one cybersecurity briefing, complete the form and we'll get in touch to schedule a time that works best for you.

Turnkey Managed IT for Small Businesses
Bulletproof 365 layers Bulletproof’s proven cybersecurity expertise over the best-in-breed Microsoft 365 productivity tools that power modern workplaces for small businesses. Benefit from unmatched employee education, 24/7 IT support, advanced security protection, and of course seamless integration (taking the headache out of IT).
Get Bulletproof Expertise
We're here to help solve your complex IT and security problems.
Get in touch by completing this form and we'll connect you with a Bulletproof expert.


-1.png?width=1000&height=350&name=Impact%20Award%20+%20Global%20Award%20Duo%20Logos%20(5)-1.png)





