Today’s work environment is faced with cybersecurity threats that are increasing in both frequency and complexity.
![]() The number of vulnerable networks has increased as more industries go through digital transformation and implement hybrid work, opening more doors to rogue access points.
The number of vulnerable networks has increased as more industries go through digital transformation and implement hybrid work, opening more doors to rogue access points.
![]() The availability of “attack-in-a-box” tools to skilled cybercriminals and amateur threat actors alike has equipped more people to break into vulnerable networks.
The availability of “attack-in-a-box” tools to skilled cybercriminals and amateur threat actors alike has equipped more people to break into vulnerable networks.
As the overall rate of cybercrime soars, the business impact of each attack is also rising due to:
-
Increasing costs related to ransomware attacks
-
Productivity downtime during a cyberattack
-
Reputation loss from customer data breaches
-
Domain compromises resulting from ransomware attacks and business email compromises
-
Human resources required for security monitoring during a labour shortage
![]()
Article Sections
Can Your In-House IT Team Keep Up With Their To-Do List?
Cybersecurity threats are real and imminent, and businesses of all sizes can be victims. Expanding your in-house IT security resources may seem like a logical next step, but the resource investment required to do so is out of reach for most non-enterprise businesses.
Fortunately, mid-size businesses have excellent, attainable options to ensure their data and systems are protected.
IT departments today are tasked with more than ever — supporting remote workforces, eliminating rogue wireless devices on their networks, developing infrastructure to enable digital transformation, monitoring for cybersecurity threats, and much more.
This growing to-do list has revealed two main issues many businesses are dealing with.

The first one is that as the responsibility list expands in length and complexity, the team is likely not growing as fast as the list. Also, leaner IT teams can’t afford to become specialists in every area — a wide range of knowledge is required to do the job. It’s hard enough to fill open positions with qualified generalists let alone an array of specialists.
The second major issue with an increasingly over-extended IT team is that something’s got to give in terms of priority. The items that remain at the top of the priority list are probably going to be the ones that are causing the phones to ring or the emails to pile up right this minute. This is a reactive way of working, which ends up causing more work for the team in the end.
How can IT teams shift from a rushed, high-pressure, reactive way of working to a proactive approach? In terms of IT security, educating the workforce on best practices is a good start. But even full adherence to the best policies doesn’t guarantee full protection. To complement the education of cybersecurity best practices, continuous prevention, detection, and protection efforts need to be in place.

Can You Afford 24/7 In-House Threat Detection and Response?
Cybercriminals don’t just work 9-5 on weekdays, so even if an in-house team member is alerted that a threat has been detected, what is the timeline between detection and containment? That timeframe is the most critical period, as it could mean the difference in the impact size of an incident.
Today’s cyberattacks are most often human-led, so an initial threat could mean that it’s a first attempt and action is required to protect the data on your network.
Hiring IT security specialists with the depth of knowledge and the tools required to proactively defend businesses against modern threats is simply out of reach for most non-enterprise businesses. To effectively run a 24/7 threat monitoring program that can detect threats, contain them, and take preventative action immediately, a security operations centre (SOC) is required. Beyond the expert personnel, a SOC requires costly equipment to ensure a successful threat response strategy and can take a year or more of setup time to become fully operational.
SOC Staffing At A Glance
- A full-time security analyst investigates and mitigates 3 incidents per hour, with a time investment of 20 minutes per incident.
- Each user of your corporate software and systems generates approximately 1 incident per month.
- For an organization with 1,500 employees, about 500 hours per month will be spent investigating security incidents.
- One IT specialist works about 160 hours per month.
- Assuming your IT team has no other duties and team members never take vacation or sick days, a minimum of 6 specialists would be required. (3 FTE, 2 additional specialists for redundancy, training, and availability to staff a 24/7 operation, 1 manager)
- Required resources scale up along with total employee count — an organization with 6,500 employees would need 15+ full-time IT security specialists.
.png?width=1859&name=CEOC-Suite%20eBook%20(5).png)
Can You Afford Not to Have 24/7 Threat Detection and Response?
The fact of the matter is that most mid-sized businesses can’t survive the devastating financial and reputational consequences of a serious breach — and yet, many mid-size businesses continue to leave their cybersecurity doors unlocked, practically inviting a cyberattacker to walk in and ransack their business.
If this describes the situation you’re in today, you’re not alone. Cyberattacks have increased 400% compared to pre-coronavirus time. The increase combined with the fact that many mid-size businesses do not have any cybersecurity plan in place at all means most organizations are in big trouble.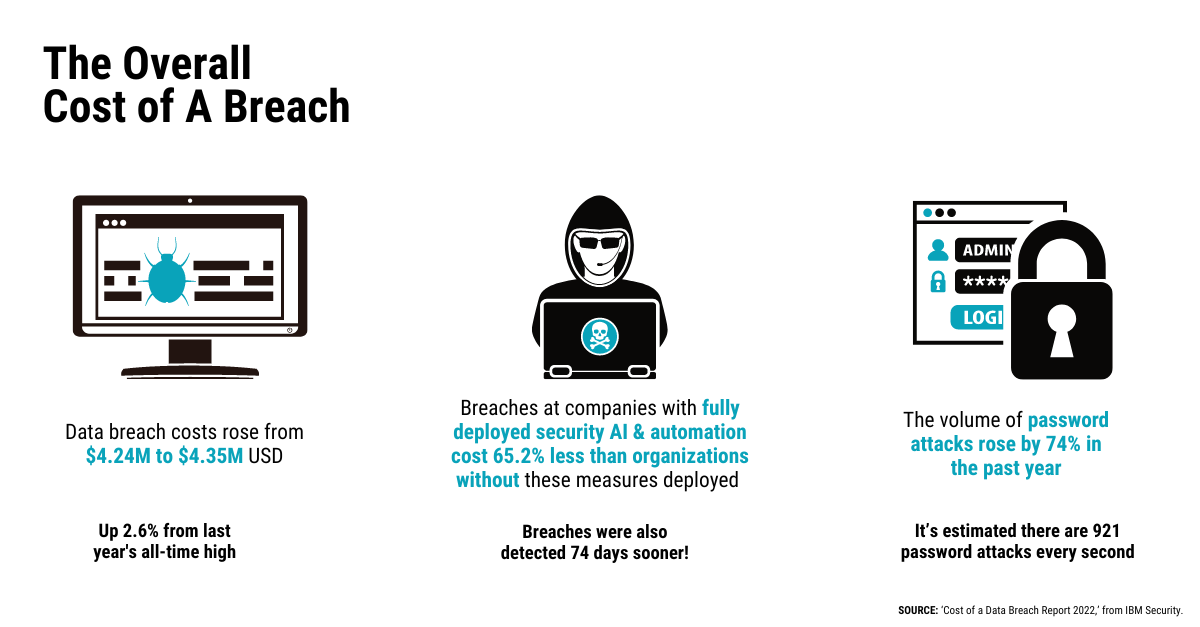

What Business Leaders Can (And Should) Do Next
It’s clear that expanding an in-house IT security team to handle every cybersecurity threat is out of reach from a financial and human resource perspective.
Finding third-party security experts that have a fully-equipped SOC with a team of experienced and knowledgeable professionals at the helm can be challenging, but well worth the investigative effort. Securing third-party expert threat detection and response means your business will be protected 24/7, no matter how time- or resource-constrained your in-house IT team may be.
For this reason, most mid-size businesses choose a third party to handle IT security, such as a Managed Security Services Provider (MSSP). Many MSSPs use a “Best-of-Breed” approach, layering on integrations as a company grows or as an industry shifts (e.g. moving to the cloud, enabling remote and hybrid workforces). Each integration demands an overwhelming amount of human attention to analyze various alerts and perform security architecture maintenance — and yet blind spots still exist for cybercriminals to prey on.
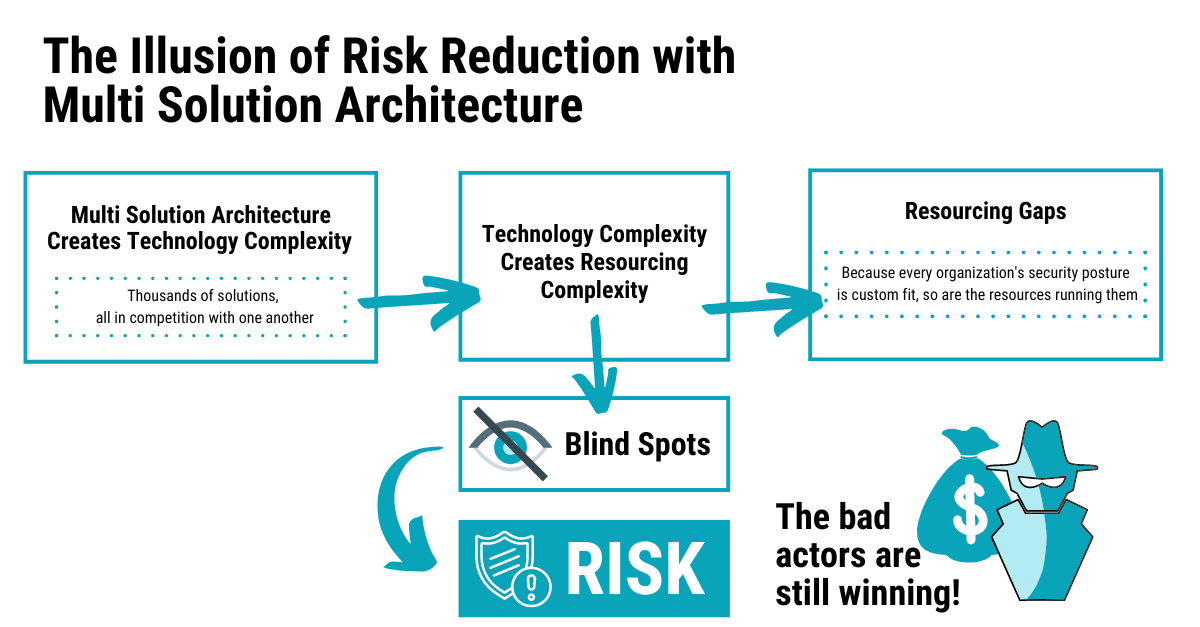
Those third-party cybersecurity experts who have moved from a “Best-of-Breed” to a “Best-of-Platform” approach (including Bulletproof), have taken a step back to view an organization’s IT security needs holistically. Using a modern, natively integrated platform approach to security still relies on human cybersecurity expertise, but with the benefits of automation to ensure complete end-to-end coverage to mitigate attacks.
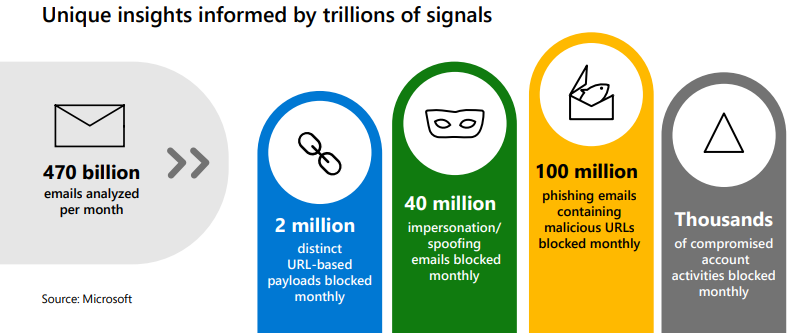
By outsourcing to a trusted team of IT experts who use a Best-of-Platform approach to cybersecurity, you’ll greatly reduce your risk of a cyberattack while increasing ROI.
Bulletproof uses a “Best-of-Platform” approach with Microsoft’s Security platform to fully integrate and defend your network against cyberthreats such as ransomware attacks, BEC, data breaches, supply-chain attacks, and other types of malware.
As the 2021 Microsoft Global Security Partner of the Year, Bulletproof is happy to discuss how our cybersecurity expertise can be used to mitigate the risk of a cyberattack on your network. Contact us to get started with a personalized security assessment.
If you were hit by a ransomware attack, would you know what to do?
If you were hit by a ransomware attack, would you know what to do?
On Friday the 13th, in the middle of a pandemic, a cyberattack threatened to bring a city’s entire network—and crucial services—to a halt.
Meet the city that refused to pay hackers and learn how quick action, teamwork, and the comprehensive visibility and security of our B365E solution saved the day.
-2.png?width=200&height=250&name=Untitled%20design%20(10)-2.png)
Supercharge Your Security Operations
Enhance the efficiency of your Security Operations Center (SOC) by integrating cutting-edge threat intelligence that provides real-time insights into emerging threats and vulnerabilities.
This advanced intelligence enables your team to anticipate and respond to potential security breaches with precision and speed. Additionally, implement automated attack disruption technologies that swiftly neutralize sophisticated cyber threats, such as ransomware, before they can inflict damage.
Get Bulletproof Expertise
Enhance your security posture and ensure compliance with cutting-edge tools, deep expertise, and streamlined processes.
Get started on your security journey today.
Fill out the form, and our team of experts will reach out within 24 hours for a brief introductory call to discuss next steps.


-1.png?width=1000&height=350&name=Impact%20Award%20+%20Global%20Award%20Duo%20Logos%20(5)-1.png)


.png?width=496&height=279&name=Engagements%20CTA%20(1).png)
