ARTICLE
Best-of-Breed is No Longer Best
Through decades of experience in providing security solutions to customers, Bulletproof security experts have come to recognize a critical truth: the best-of-breed point solution model to secure enterprise organizations is no longer the best approach to protection.
What we have learned—and lived—is that the true “best” security posture is one that tightly integrates to provide a complete, holistic picture of the organization with no overlap or conflict in the process for investigation of or response to incidents. While other solutions can provide a “single pane of glass” for investigation, what sets this new best-of-platform model apart is the speed of incidence-to-response that automation provides. This great reduction in risk and increase in response speed is the ROI.
Automated Response Across the Entire Platform
No one wants to miss threats by ignoring things, but human time wasted on chasing dead ends leads to longer response time for actual incidents. Automation helps correlate, consolidate, and analyze a high volume of alerts, enabling your human analysts to spend their time on the investigation and remediation of complex issues. Automated response across the entire platform—which is the only chance for successful mitigation of a complex human-led breach or attack—can only be achieved by a platform that provides complete end-to-end coverage, from endpoint to infrastructure, identity to cloud.
"The threat landscape has evolved to a point where the best-of-breed model is now creating a false sense of security."
Article Sections
A Best-of-Platform Solution
At Bulletproof, we fulfill the promise of best-of-platform protection with the Microsoft Security platform. In our experience, it offers unmatched integration and automation.
The security industry is inundated with acronyms, and the latest to hit the market is XDR, or Extended Detection and Response. It is defined by Gartner as “a SaaS-based, vendor-specific security threat detection and incident response tool that natively integrates multiple security products into a cohesive security operations system that unifies all licensed components.” This industry shift toward a platform approach is in recognition of the gaps that exist in the legacy best-of-breed model, particularly as it relates to response capabilities.
Microsoft has been a leader in this space well before the acronym was coined and recently rebranded their security suite of products under the Microsoft Defender brand to better reflect the pre-existing integration across its platform. Microsoft Defender includes coverage across all areas of a customer's computing environment, including:
- Identity (on cloud and on prem)
- Infrastructure (on cloud and on prem)
- Productivity (O365)
- Application (SQL Server)
- Endpoint (traditional and mobile)
- OT operating environments
No other security vendor can offer such a wide breadth of integrated coverage for the entire enterprise.
Complete Integration the Key to Success
Integrating the Microsoft Defender toolset with Microsoft’s Sentinel SIEM/SOAR unlocks full end-to-end visibility across all resources (including edge network) with correlated, prioritized alerts based on the deep understanding Microsoft has of its products, its vast threat intelligence capabilities, and artificial intelligence/machine learning (AI/ML). Beyond more accurate alerting, this native integration also enables intelligent automated response and containment activities across the entire platform, something no other vendor can match.
The Microsoft Defender suite of products provides this complete solution, and when integrated through a single pane of glass (Microsoft’s Sentinel SIEM/SOAR), allows deep investigation, cross-correlation between components, and automatic remediation and mitigation of security incidents. Most SIEMs take logs from multiple sources. Microsoft Sentinel goes a step further. Now you can get a unified view of all the inputs in Sentinel, and seamlessly drill down into an incident in Microsoft 365 Defender.
%20is%20SaaS-based%2c%20vendor-specidic%20security%20threats%20detection%20and%20incident%20response%20tool%20that%20natively%20integrates%20multiple%20security%20products%20into%20a%20cohesive%20secur.png?width=350&height=700&name=Extended%20Detection%20and%20Response%20(XDR)%20is%20SaaS-based%2c%20vendor-specidic%20security%20threats%20detection%20and%20incident%20response%20tool%20that%20natively%20integrates%20multiple%20security%20products%20into%20a%20cohesive%20secur.png)
The Biggest Benefit of Best-of-Platform : Automated Response
Human-operated ransomware campaigns are one of he most impactful trends in cyberattacks today, and they pose a significant and growing threat to businesses. In these hands-on-keyboard attacks, which are different from auto-spreading ransomware like WannaCry or NotPetya, adversaries employ credential theft and lateral movement methods traditionally associated with targeted attacks like those from nation-state actors. They exhibit extensive knowledge of systems administration and common network security misconfigurations, perform thorough reconnaissance, and adapt to what they discover in a compromised network.
These attacks are known to take advantage of network configuration weaknesses and vulnerable services to deploy ransomware payloads. And, while ransomware is the very visible action taken in these attacks, human operators also deliver other malicious payloads, steal credentials, and access and exfiltrate data from compromised networks.
The Impacts of a Ransomware Attack
News about ransomware attacks often focuses on the downtimes they cause, the ransom payments, and the details of the ransomware payload, leaving out details of the oftentimes long-running campaigns and preventable domain compromises that allow these human-operated attacks to succeed.
Based on our investigations, these campaigns are unconcerned with stealth and have shown that they could operate unfettered in networks. Human operators compromise accounts with higher privileges, escalate privilege, or use credential dumping techniques to establish a foothold on machines and continue unabated in infiltrating target environments.
Human-operated ransomware campaigns often start with “commodity malware” like banking Trojans or “unsophisticated” attack vectors that typically trigger multiple detection alerts; however, these tend to be triaged as unimportant and therefore not thoroughly investigated and remediated. In addition, the initial payloads are frequently stopped by antivirus solutions, but attackers just deploy a different payload or use administrative access to disable the antivirus without attracting the attention of incident responders or security operations centers (SOCs).
"Automated response is the best defense against complex human-operated attacks."
The bottom line from what we’ve seen in the wild? Automated response is the best defense against complex human-operated attacks.
Microsoft Defender for Endpoint is the only solution that provides AI-based automated response natively, right out of the box, which can automatically investigate, evaluate, and respond to threats. The ability to respond to threats from the Defender for Endpoint portal, whether manual or automatic, is a key differentiator from other solutions. The deep integration provides visibility and control beyond what other solutions can offer.
"Studies show that automated response capabilities can detect threats in minutes, not months."
Automated Incident Remediation in Action
An example of automated remediation that we have seen is a scenario in which a workstation is used to browse a website and download a file which turns out to be malicious when it is executed. Defender for Endpoint detects this and alerts the Defender for EndPoint portal, where Microsoft Sentinel, based on policies in place, automatically instructs the workstation to isolate itself from the rest of the network until it can be investigated thoroughly. This is just one example of how automated remediation shortens the time between detection and response of an issue.
The alternative to this is the legacy scenario, whereby a security officer or other IT personnel are alerted to a potential incident, time is spent investigating the received alert, a decision is finally made to investigate the workstation more thoroughly, and someone either manually removes the workstation from the network, or makes changes to a network switch or other architecture to isolate the workstation. This takes time—time that could allow something malicious on a workstation to traverse laterally throughout the network and affect multiple devices. This is, unfortunately, the scenario that we are often faced with when using best-of-breed solutions that do not have built-in, automated response mechanisms.
The bigger issue, however, is if credentials were captured before the workstation was isolated. If there is no integration between security solutions, even though the machine has been isolated, the identities on the machine have not. This means the attacker can simply jump directly into the cloud, advancing the attack.

Microsoft Defender
Defender for Endpoint is a built-in component of Windows 10, with complete integration and visibility into the Windows OS. No other XDR can provide the same level of visibility and control on the workstation. With this built-in approach, there are no agents to deploy and manage. The features already exist in the OS, which also makes them harder for bad actors to bypass or disable.
Further, Cloud Access Security Broker (CASB)-like functionality is built into Defender for Endpoint, which allows automatic protections such as blocking a workstation from accessing a malicious website that has been identified by Microsoft’s Threat Intelligence. It also integrates tightly with Microsoft’s CASB, Microsoft Defender for Cloud Apps, which provides additional control and visibility into a workstation or user’s use of other cloud services; even non-Microsoft services like Dropbox, SalesForce, etc.
This integration of Defender for Endpoint with Microsoft Defender for Cloud Apps also allows organizations to sanction or disallow the use of certain cloud SaaS apps or services for groups of users or for all users. This can’t be done with security products that aren’t integrated.
Other out-of-the-box automated remediation and mitigation techniques that can be deployed on a workstation through the use of Defender for Endpoint include:
- Collect investigation package
- Isolate device (this action can be undone)
- Offboard machine
- Release code execution
- Release from quarantine
- Request sample
- Restrict code execution (this action can be undone)
- Run antivirus scan
- Stop and quarantine
The Best-of-Platform Approach
Bulletproof utilizes Threat Hunting techniques as a key component of both its reactive and proactive services within our Bulletproof 365 Enterprise service offering. Through the use of Jupyter Notebooks, we create repeatable playbooks that can be used to perform Threat Hunting exercises. Many examples of these notebooks are being published online through the security community to help build out threat hunting toolboxes, again shortening the time to detection through sharing of vital information and techniques.
Evidence found through threat hunting, or through detections from the various sensors in the M365 Security toolset, can be correlated between Microsoft Sentinel, Defender for Endpoint, Defender for Office 365, and Microsoft Defender for Cloud Apps, among other components, to show the entire incident in one pane of glass.
Defender for Endpoint also has direct integration with Microsoft Data Loss Prevention (DLP) technologies, enabling further insights and capabilities when customers are implementing governance and compliance controls within their organization.

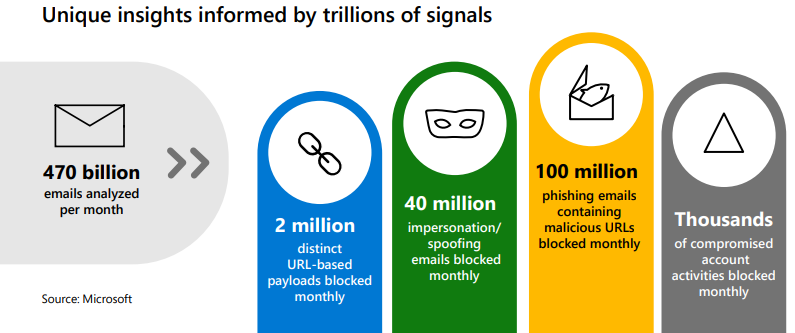
Microsoft Defender for Office 365 P2: Automation Beyond Email
It is no surprise that email is still the primary attack mechanism for malicious software and bad actors. Protections for email environments are paramount and considered table-stakes for most organizations’ security programs. Many solutions in the market can help reduce the number of phishing emails, malicious attachments, files, and links that your users come into contact with, and many of them do a respectable job of detecting and preventing these threats from reaching your user base. But, Microsoft Defender for Office 365 P2 takes its coverage further than its competitors.
As an integral component of the Microsoft 365 Security suite, Microsoft Defender for Office 365 P2 not only protects email, but it also protects other productivity applications such as OneDrive, SharePoint, and Teams. Microsoft Defender for Office 365 P2 will detect when malicious files (or even web links) are pasted to these applications, removing them before users can innocently click on them and find themselves in trouble. This closes a gap that other products suffer from.
Competitor solutions focus exclusively on email, and some of them only detect malicious items as they pass through the protection gate. They can’t reach into your users’ mailboxes and remove links that become weaponized AFTER the email was delivered.
Microsoft Defender for Office 365 P2 is very tightly integrated with the rest of the Microsoft security stack and provides automated response mechanisms to reduce the time between incident detection and response. The automated investigations and responses by Microsoft Defender for Office 365 can include the following actions, right out of the box:
- Blocking of URLs (time-of-click): Microsoft will check out a URL before a user can access it to ensure the user does not accidentally get themselves into trouble
- Soft delete email messages or clusters, even after they have been delivered
- Quarantine email/attachments: The ability to quarantine emails/attachment is table stakes for mail protection
- Turn off external mail forwarding: Forwarding mail to an external mailbox is a malicious technique that is often used to “spy” on company emails in an attempt to gather information for a ransomware or phishing campaign. Microsoft Defender for Office 365 can spot this and turn this functionality off on a mailbox automatically
There are other capable email hygiene solutions out there, but they don’t protect key areas that Microsoft Defender for Office 365 P2 does—namely, Teams, SharePoint, and OneDrive. This becomes more and more important as your organization scales out the use of these services, invites external users into your Teams and SharePoint environments, and allows access to all of these environments from devices that you do not directly manage.
DID YOU KNOW?
Microsoft Defender for Office 365 has been named a Leader in The Forrester Wave™: Enterprise Email Security, Q2 2021.
Reduce Risk with Best-of-Platform
Bulletproof 365 Enterprise is architected to provide the most complete security visibility and incident response capabilities possible.


Discover More

TRANSFORM YOUR SOC TODAY
As security experts, we choose Microsoft Sentinel because we've seen firsthand how putting a modern SIEM solution in place transforms the SOC in businesses just like yours. Whether you need an assessment, are ready to deploy, or need customization or managed security services, we're ready to help you optimize threat detection, investigation, and response.
Learn more about Bulletproof 365 Enterprise (B365E), our intelligent MXDR Security powered by Microsoft 365 and Microsoft Sentinel. Get proactive protection and responsive security with 24/7 security incident triage, investigation and response and advanced threat hunting to secure any gaps.
If you were hit by a ransomware attack, would you know what to do?
On Friday the 13th, in the middle of a pandemic, a cyberattack threatened to bring a city’s entire network—and crucial services—to a halt. Meet the city that refused to pay hackers and learn how quick action, teamwork, and the comprehensive visibility and security of our B365E solution saved the day.
Bulletproof Credentials
- Bulletproof named to CRN's Managed Services MSP 500 List for 2026
- Bulletproof named to CRN's Managed Services MSP 500 List for 2025
- 2025 Microsoft Intelligent Security Association Excellence Award Finalist, Security Trailblazer
- 2025 Municipal Information Systems Association BC - Associate Partner of the Year
- 2024 Microsoft Intelligent Security Association Excellence Award Winner, Security Trailblazer
- 2021 Global Security Partner of the Year Winner, Microsoft
- 5X Microsoft Canada Security IMPACT Award Winner
- 20+ years of IT, security, & compliance knowledge serving various industries across North America
- Global state-of-the-art 24/7 Security Operations Centers (SOC), 24/7 Service Desk Support, Network Operations Center (NOC), & Technology Operations Center (TOC)
-
Long-standing Microsoft Solutions Partner for Modern Work, Digital & App Innovation Azure, Infrastructure Azure, Data & AI, and Security with specializations in Cloud Security, Identity & Access Management, Data Security, and Threat Protection.
-
Member of the Microsoft Intelligent Security Association
-
Awarded General Services Administration (GSA) Multiple Award Schedule (MAS) with holder of Highly Adaptive Cybersecurity Services (HACS)
-
Certified Cybersecurity Maturity Model Certification (CMMC) Practitioner Organization

Vasu Jakkal, CVP, Microsoft Security
Get Bulletproof Expertise
We're here to help solve your complex IT and security problems. Get in touch using this form and we'll connect you with a Bulletproof expert.



